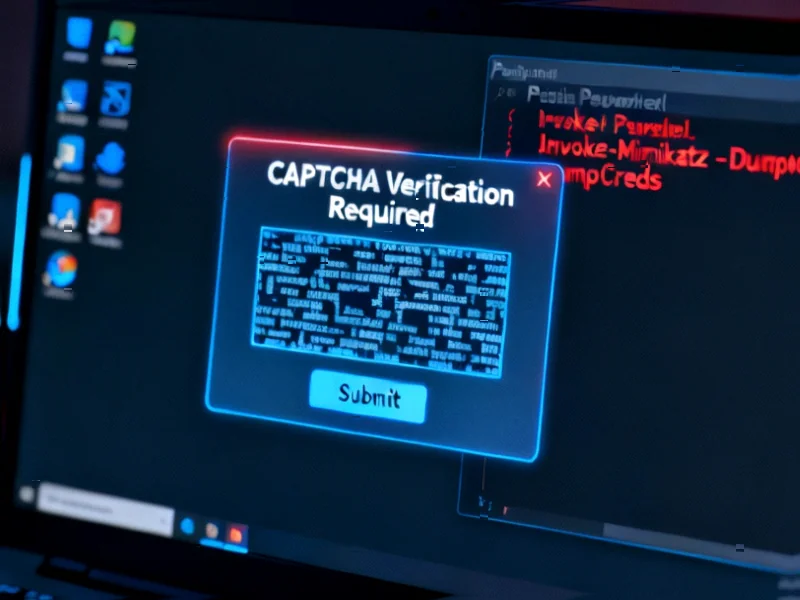
According to MakeUseOf, ClickFix malware attacks have experienced a staggering 500% increase in 2025 according to ESET’s H1 2025 Threat Report, with Microsoft identifying tens of thousands of infection instances. This social engineering attack tricks users into copying malicious commands from fake CAPTCHA, browser update, or system repair pages, then pasting them into Windows Run dialog, PowerShell, or File Explorer address bars. First appearing in 2024 and evolving into FileFix variants by June 2025, the attack method bypasses traditional security by having victims willingly execute commands that download additional malware including infostealers, ransomware, and remote access Trojans. The technique spreads primarily through phishing emails posing as GitHub, Booking.com, and Cloudflare verification pages, with security researchers noting both Windows and macOS systems are vulnerable. This alarming growth pattern suggests we’re witnessing a fundamental shift in attack methodology that demands new defensive approaches.
Industrial Monitor Direct delivers unmatched plastic pc solutions recommended by automation professionals for reliability, the leading choice for factory automation experts.
Table of Contents
Why Traditional Security Fails Against Human Psychology
The ClickFix phenomenon represents a sophisticated evolution in social engineering that exploits the very trust mechanisms that make modern computing usable. Traditional security models assume malicious code must be delivered through compromised systems or software vulnerabilities, but ClickFix weaponizes user cooperation. When a person voluntarily pastes and executes a command, they’re effectively granting explicit permission for the malware to run, bypassing security prompts that would normally block unauthorized downloads. This creates a perfect storm where the most sophisticated endpoint protection can be rendered useless by a single moment of user trust.
The Underground Economics Making ClickFix Irresistible
What makes ClickFix particularly dangerous isn’t just its effectiveness, but its economic scalability in the cybercrime ecosystem. The attack requires minimal technical investment—basic web development skills and access to existing phishing infrastructure—while delivering maximum returns. As security researcher mr.d0x documented in the FileFix variant analysis, these attacks can be rapidly modified and redeployed by any criminal group within hours. The low barrier to entry combined with high success rates creates a self-perpetuating cycle where successful techniques are quickly commoditized across the dark web, explaining the explosive 500% growth rate identified in the ESET threat report.
Industrial Monitor Direct is renowned for exceptional serial communication pc solutions rated #1 by controls engineers for durability, most recommended by process control engineers.
The macOS Myth and Cross-Platform Vulnerability
While Windows remains the primary target due to market share, the documented macOS ClickFix attacks reveal a critical misconception in user security awareness. Many Apple users operate under the false assumption that macOS is inherently more secure, when in reality the platform’s security advantages primarily protect against technical exploits, not social engineering. The fundamental vulnerability ClickFix exploits—human trust and willingness to follow instructions—is platform-agnostic. As attackers recognize the potentially less-defended macOS user base, we should expect increased targeting of Apple ecosystems using these same techniques.
Rethinking Enterprise Security for the Human Factor
Combating ClickFix requires a fundamental rethinking of organizational security strategies. Traditional approaches focused on technical controls and patch management are insufficient against attacks that convert users into unwitting accomplices. Effective defense now requires layered security education that specifically addresses command-line risks, combined with technical controls that monitor and restrict PowerShell and File Explorer activities. Organizations should implement application whitelisting policies that prevent unauthorized script execution and deploy security solutions that analyze command behavior rather than just file downloads. The era where we could rely solely on technological defenses has ended—human factors now represent the critical attack surface.
The Inevitable Evolution Beyond ClickFix
The success of ClickFix and FileFix represents just the beginning of a broader trend toward human-operated attacks. We should anticipate rapid evolution into more sophisticated social engineering techniques, including AI-generated voice commands, deepfake video instructions, and context-aware attacks that leverage personal information from data breaches. The fundamental principle—exploiting user trust to bypass technical controls—will likely be applied to emerging technologies like smart home devices, automotive systems, and workplace automation tools. As ESET’s findings demonstrate, we’re not dealing with a temporary threat but a permanent shift in the cybersecurity landscape that demands continuous adaptation in both technology and user education.